My son was playing Watch_Dogs on our PS4 Tuesday, and had just completed a takedown of a Gang Hideout, and went to spend his freshly minted skill point only to discover that ALL of his skills, money, outfits, etc had just disappeared from his gamer profile. He still had actual access to some of his skills (blowing a steam main, but not focus), so his actual gameplay is now critically impacted. And he can’t use his new skill points to backfill some of those critical skills because primary skills like Profiling are blank (although this is another skill he can actually use), and not selectable.
Category: How it works
The topic of Net Neutrality revisited…
I wanted to take the time to communicate to you the single most important action that you need to take to retain your existing rights to free speech, but may not even have know about until you read this article.
Currently in front of the FCC is a proposal for changing of the current definition of Net Neutrality. The FCC has issued a 120 Day Comment period, which has been extended recently due to the incredible influx of community comments so far. The new deadline is September 15th.
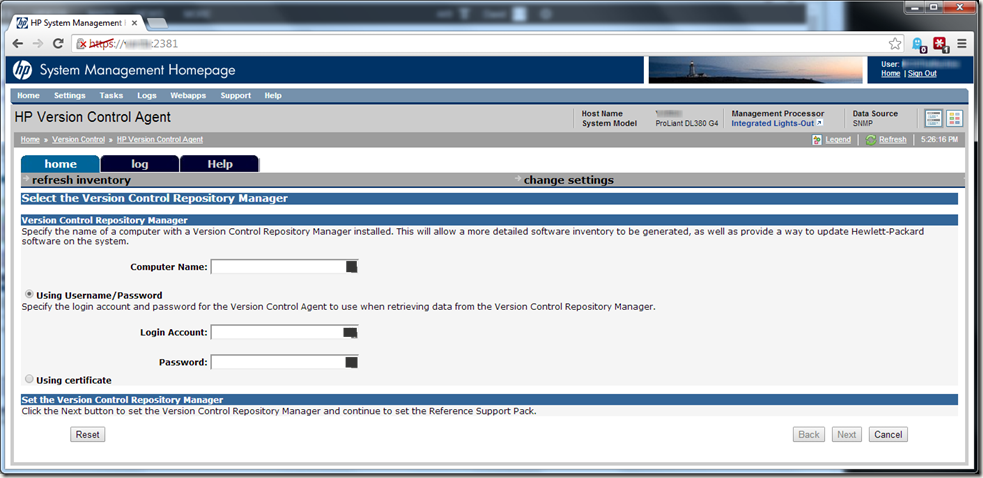
When you can’t Connect HP Version Control Agent (VCA) to the Version Control Repository Manager (VCRM).
As a self-taught Systems Administrator, I tend to learn by the process of trial and error. And boy have I erred a lot recently. I’ve been banging my head against this particular brick wall (not being able to connect the HP VCA to the HP VCRM) in earnest the last couple of weeks:
It seemed that no matter how I input the info on the screen above, the two would never see each other. Credentials were confirmed, permissions vetted, yet every time I filled out this screen and clicked “next”, I would inevitably get the message “The specified repository, servername.domainname.com, is invalid or not reachable.”. I was just going around and around, in a downward spiral that didn’t bode well for my sanity.
I was therefore EXTREMELY happy when I found this gem in the HP Systems Insight Manager Support forums in a post talking about an upgrade from version 7.2.2.0 to 7.3.0.0:
I’ve got answer form HP TS regarding HP VCA 7.2.2.0 working with HP VCRM 7.3.0.0
I did not got full answer of root cause of this issue but form provided command I suspect that it is is realted with SSL Cipher configuration.
For me these commands solved th issue.
Please try run follwing commands on server with HP VCRM 7.3.0.0:
C:\HP\hpsmh\bin>smhconfig.exe -Z ALL:!ADH:!EXPORT56:!EXPORT40:DES-CBC3-SHA:RC4-MD5:RC4-SHA:RC4+RSA:+HIGH:+MEDIUM:-SSLv2:+EXP:!LOW:!eNULL:!aNULL
C:\HP\hpsmh\bin>smhconfig.exe -r
For me these commands solved the issue.
Sadly, I wasn’t sure this would resolve my problems, since I had never been able to get VCA and VCRM to talk initially, therefore my problems obviously were not due to an upgrade like everyone else’s. However, some of the connectivity issues mirrored those I was experiencing, so I applied the fix as a batch-file (copy/paste commands to text file to avoid fat-fingering any characters, saved as .BAT file, issued command line “run as administrator”), and voila! Suddenly I can connect the two together!
Sadly, I have no breakdown of the intimate details involved with what the commands do exactly, or how they accomplish the resolution, but it was made clear that the problem was due to an SSL Cipher configuration. My take is that it appears that HP had actually removed some expected ciphers from 7.3.x.x of VCRM, which then prevented the communication from VCA Agents.
But, all good now!
Seen a .menc file before?
If you’ve ever seen a .menc file before, you probably saw it on an external memory card that you pulled out of your Windows Phone device. Â
Essentially, .menc (Mobile Encryption) files are just your personal data (the PIM.VOL file that contains all of your Contacts for example) that are encrypted. The extension of .menc lets the Operating System (OS) know which files are encrypted, and whether or not they can be opened by the user.  To do so, the previously recorded key (user password) must match the key provided by the user when unlocking the device. But you won’t see those .menc files, because they are typically hidden by the OS so as not to be visible to the end-user during casual browsing.  If you ever chose to encrypt the files you store on your external storage (external memory card, etc), then they may be visible if you took that card to another computer or device for viewing.
If you’re trying to recover those files, then you have to meet some rather special requirements in order to proceed. Unfortunately, if you have Hard Reset the device, or have a different device than the one that the files were originally created on, then the encryption/decryption keys are now lost or no longer the same, then sadly your files are totally inaccessible.Â
However, if you have access to the same device that the .menc files were originally created on, and you have NOT performed a Hard Reset on the device, then you can still salvage the files:
- Turn the storage card encryption off: Go to Start > Settings > System > Encryption (varies by your Operating System version) and uncheck the “Encrypt files when placed on a storage card†box. From this point forward, all NEW files created on that card will be unencrypted, but existing files will still be encrypted.
- Next, bring-up your favorite File Explorer, then browse to your Storage Card. Make a new folder on the storage card, and call it “OLDDataâ€. This folder will, of course, be unencrypted.
- Now, find whatever files you want to decrypt and copy them into this folder. Those files will be decypted as they copy into the new folder. You can now read these files on any other computer or phone.
Congratulations, you’ve just saved some data.  Hopefully it will turn out to be highly important data, which will make your victory taste just a little bit sweeter…
Trying to setup a good Dynamic DNS solution
Since I had to give-up my Static IP Address as part of my UVerse installation, I am looking around for a way to setup a Dynamic DNS Solution that would provide consistent access to my Home Network from the outside world.
The Problem: The challenge is that since I am now using PPOE to connnect to AT&T, my IP Address changes frequently.  Since the IP Address changes frequently, I cannot consistently know when the IP Address changes, and what it changes to.Â
The Partial Solution: Enter Dynamic DNS, or DynDNS. This is a solution that works to automatically detect the new IP Address assignment and update DNS “Dynamically” whenever a change occurs. The Router (or software package running on one of the Private Network PCs) would detect this change, then notify the DynDNS Host Server (which is always consistent) of the new IP Address. The downside of this particular solution is that the DynDNS Host Server will traditionally only allow the new user to pick a name for a subdomain of their existing domain choices (in my case, helpdesk.dyndns.org), and some users like myself do not like this kind of restriction. Â
The Rest of the Solution (I hope):Â So I’m working with my provider to see if I can create a new subdomain of matson-consulting.com and have that setup to redirect incoming traffic to the helpdesk.dyndns.org URL.
I hope I can get this setup…
Security in a Mobile World part-4 Posted

Security on the PocketPC platform is a great deal different than your laptop. Security issues considered minor on the Laptop platform like Physical Access, Application/Data Access, and Theft/Loss Mitigation are more substantial on the PocketPC platform, because the PocketPC is infinitely easier to steal than a laptop. And larger issues on the Laptop like Firewalls, AntiVirus, and AntiSpyware become less predominant because the PocketPC platform offers less of a potential target for hackers. Because there is currently more interest in cracking Windows PC data and applications, the PocketPC platform is relatively safe, but that will change soon enough.
If you would like to read the entire 4th part of this article, click here.
Security in a Mobile World part-3 Posted

It is a well known fact that most every Laptop user could stand to improve their privacy (and overall security) when utilizing their PC for everyday use. This installment is geared towards getting you started on the right path towards accomplishing this goal.
If you would like to read the entire 3rd part of this article, click here.
Security in a Mobile World part-2 Posted

Public wireless hotspots are, by definition, meant to be public, and so it goes that private hotspots are meant to be private, regardless as to whether or not the hotspot is encrypted to keep unauthorized users out. This is the same as recognizing the difference between a grocery store and a residential home. A grocery store is open to the public, and you can walk through the door and browse among the aisles to your hearts content. Likewise, it is generally understood that it is completely unacceptable for someone to just walk into another person’s home unannounced. It needs to be understood and accepted that a private Wi-Fi LAN is essentially an extension of someone’s personal property.
If you would like to read the entire 2nd part of this article, click here.
Security in a Mobile World part-1 Posted

Security is a multilevel concept, in both the mindset and it’s practical application. The mindset refers to keeping the concepts of security at the front of your mind while you go through your daily activities. The practical application is Security itself. For now, I will only attempt to touch on the important levels (under the heading of Practical Application) that Mobile Users need to consider in today’s environments. Later I will touch on the mindset aspect of Security.
If you would like to read the entire 1st part of this article, click here.
Anatomy of the DHCP assignment process
1.) The first (due to it being a "default" setting for most network adapters) and best way to configure your network connection is to enable a process called DHCP (for "Dynamic Host Configuration Protocol"), also referred to as a "Dynamic IP Assignment", because the DHCP server can change assignments on an "as needed" basis.
2.) The second way it to manually specify your settings, also referred to as a "Static IP Assignment", because the system will forever keep your manual assignment until you tell it otherwise.