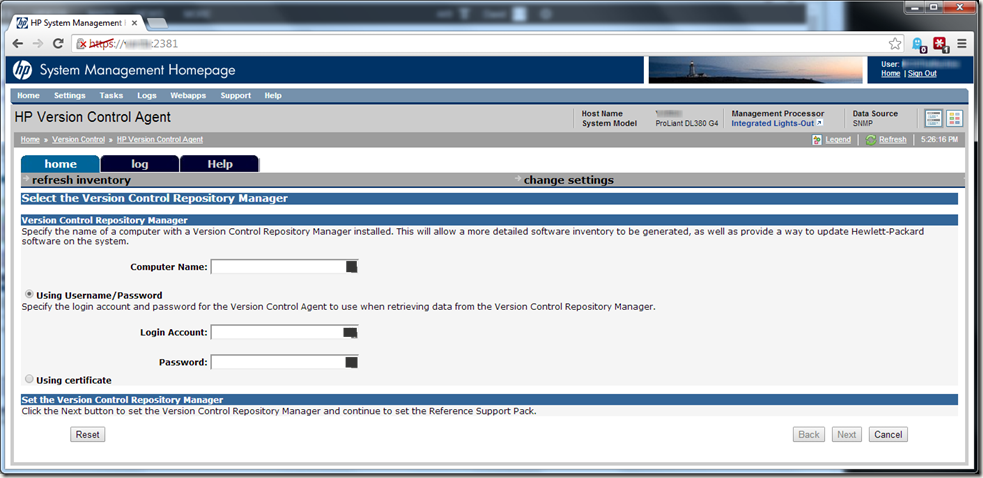
As a self-taught Systems Administrator, I tend to learn by the process of trial and error. And boy have I erred a lot recently. I’ve been banging my head against this particular brick wall (not being able to connect the HP VCA to the HP VCRM) in earnest the last couple of weeks:
It seemed that no matter how I input the info on the screen above, the two would never see each other. Credentials were confirmed, permissions vetted, yet every time I filled out this screen and clicked “next”, I would inevitably get the message “The specified repository, servername.domainname.com, is invalid or not reachable.”. I was just going around and around, in a downward spiral that didn’t bode well for my sanity.
I was therefore EXTREMELY happy when I found this gem in the HP Systems Insight Manager Support forums in a post talking about an upgrade from version 7.2.2.0 to 7.3.0.0:
I’ve got answer form HP TS regarding HP VCA 7.2.2.0 working with HP VCRM 7.3.0.0
I did not got full answer of root cause of this issue but form provided command I suspect that it is is realted with SSL Cipher configuration.
For me these commands solved th issue.
Please try run follwing commands on server with HP VCRM 7.3.0.0:
C:\HP\hpsmh\bin>smhconfig.exe -Z ALL:!ADH:!EXPORT56:!EXPORT40:DES-CBC3-SHA:RC4-MD5:RC4-SHA:RC4+RSA:+HIGH:+MEDIUM:-SSLv2:+EXP:!LOW:!eNULL:!aNULL
C:\HP\hpsmh\bin>smhconfig.exe -r
For me these commands solved the issue.
Sadly, I wasn’t sure this would resolve my problems, since I had never been able to get VCA and VCRM to talk initially, therefore my problems obviously were not due to an upgrade like everyone else’s. However, some of the connectivity issues mirrored those I was experiencing, so I applied the fix as a batch-file (copy/paste commands to text file to avoid fat-fingering any characters, saved as .BAT file, issued command line “run as administrator”), and voila! Suddenly I can connect the two together!
Sadly, I have no breakdown of the intimate details involved with what the commands do exactly, or how they accomplish the resolution, but it was made clear that the problem was due to an SSL Cipher configuration. My take is that it appears that HP had actually removed some expected ciphers from 7.3.x.x of VCRM, which then prevented the communication from VCA Agents.
But, all good now!