So today I copied my private key file to a different Windows desktop machine that I use frequently, but got this error when trying to initiate a new SSH session from that desktop:
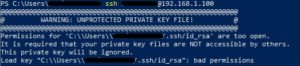
I know this should work on any number of different machines. PUB Key goes into any Server, and the PRIV Key goes into any client machine you’ll be using to access those servers. And my PUB Key worked fine on several different Servers, so this proves that both files themselves were fine, so the trouble had to be some kind of permission aspect.
The main error is “Unprotected Private Key”, but there was a secondary warning about how the file was “too open”. What this means is that there are too many people, groups, or teams who have access to the file. This supports the theory that it was a permission issue. What I did to resolve this issue is to:
- Locate the newly copied-over file in the SSH directory (under Users\YourUsername\.ssh), right-click on it, and pick Properties.
- Then, click on the Security tab, then the Advanced button towards the bottom to get this screen:
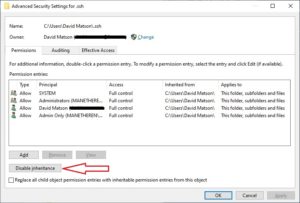
- Now, disable inherited permissions by clicking on the Disable Inherited > Convert inherited permissions
- Now, try running your SSH command again to see if this remedied the issue. If it didn’t, we’ll take the next step.
- Back at the above screen, make sure your intended profile is listed as OWNER at the top. If not, click Change and make it the appropriate username. Try SSH again.
- If this again doesn’t fix the issue, then go to the middle section and remove unnecessary users, one by one, until you can SSH into your box successfully.
As for myself, I only needed to disable inherited permissions.
I hope this works to assist you further in your Mobile World!




